This article is contributed. See the original author and article here.
Microsoft 365 enabled all its consumer to use Microsoft 365 workloads from everywhere/anywhere. Microsoft has built data center in almost all the regions which help customers to connect closed data center from your office egress and remote work locations. But still many corporates are not willing to allow their remote work force to connect directly to closet Microsoft 365 front door, and wants users to connect company VPN and then let route traffic to Microsoft 365 via egress which cause latency and performance issues. For Workloads like Microsoft teams, Its wider impact on performance which use media traffic for calls and meetings and doesn’t like to pass the traffic via VPN concentrator.
We all can agree on this that, cloud solution has given a seamless platform to connect services from anywhere but increased security and compliance threat in proportionally, And this is the fear in organization causing to not let them allow direct connectivity to Microsoft 365, even today most of the workforce is working from home due to COVID-19 outbreak.
You can use Microsoft enhanced security feature and Azure policy to enable remote users to work directly with Microsoft 365 and provide a great user experience. We must implement the security controls at mainly two level.
1. End Point Level
Using below solutions and tools, you can make sure that your user’s endpoints are secure, safe and qualifying to connect Microsoft 365 services directly.
a) Patching
An automated patching system should be in place to regularly patch the end-points like SCCM to meet the defined threshold of the compliance policy.
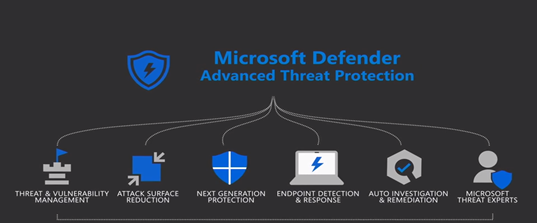
b) Defender ATP
Microsoft Defender Advanced Threat Protection is a complete end-points security tool delivers preventative protection, post-breach detection, automated investigation, and response. The beauty of this solution is, it’s not only detect the threat but immediately response and help to remediate vulnerabilities and misconfigurations.
c) Antivirus
Systems should be protected with antivirus with the latest updates. If your organization is only having windows 10 OS environment, Microsoft Defender Antivirus is automatically enabled and installed on them. But if you have mixed environment then you need to use third party antivirus with combination of Defender AV. You can go Microsoft Defender Antivirus compatibility for more details.
d) EDR (Endpoint Detection and Response)
As name suggest, when a threat is detected, alerts are created in the system for an analyst to investigate and The response capabilities give you the power to promptly remediate threats by acting on the affected entities. It’s part of Microsoft defender ATP.
e) Device Compliance
2. Azure Level
a) Azure AD Device Registration
Your device needs to be registered with azure AD. Azure AD registered devices are signed in to using a local account and additionally have an Azure AD account attached for access to organizational resources like Microsoft 365. Access to resources in the organization can be further limited based on that Azure AD account and Conditional Access policies applied to the device identity.
Administrators can secure and further control these Azure AD registered devices using Mobile Device Management (MDM) tools like Microsoft Intune.
b) Multi factor authentication
Users should be enabled to Azure MFA to access Microsoft 365 apps from external. The MFA requirement would be enforced with conditional access policy which will allow users to consume the service. The exclusion can be setup for admins accounts if required so they can connect PSshell script without MFA to manage the service without any interruption.
c) Conditional Access policy
Conditional access policy is a feature part of azure active directory to enforce the company policy based upon clients signals and decision. You need to setup conditional access policy to grant Microsoft 365 app access from external locations (Each organization may have different requirements, so they need to work with their IT security to implement it), The grant control can be enforced as per the requirements.
Setup Conditional access policy
Once you have made sure the above pre-requite for machines is in place, now you are good to configure conditional access policy to meet the requirements aligned with company IT security, which will let end user to connect M365 and teams from external.
a) Create a new CA policy
• Sign in to the Azure portal as a global administrator, security administrator, or Conditional Access administrator.
• Browse to Azure Active Directory > Security > Conditional Access.
• Select New policy.
• Give your policy a name.
b) Grant access to clients for the conditions required
c) Allow “apps”
• Select “cloud apps or actions” in the new conditional policy options
• In “Select what this policy applies to” select “cloud apps”
• Click on “Include” and pick “Select apps” radio button
• Now in the apps, you need to select the apps which you want to allow to access from external for example, Microsoft Teams.
You need to allow SharePoint and exchange apps as well as Teams use one drive, Messaging and SharePoint in background for several used cases.
How it works?
Now, I am connected with open internet and trying to login with my teams desktop app. Yes, I can sign-in successfully and use the teams over open internet.
To verify the end-end connectivity, I am checking my IP address got from service provider which is “103.86.183.43”. you can use whatismyipaddress web tool.
Now, Go into azure active directory > Sign-ins and find out the user logged-in into teams. You would see the above IP address connecting you.
As above stated, Using the strong security control you can enable your end users to access M365 and teams from outside and provide them better experience with good performance.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments