Our Latest News
Azure Maps Authentication the right way
Introduction One of the requirements when building a business application is that only authenticated users can access it. So how do you use Azure Maps in combination with authentication and authorization? When you are reading our Azure Maps docs, you...
Shopping scams are in session for back-to-school shopping
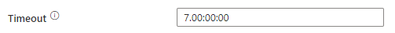
Azure Data Factory Changing Default Pipeline Activity Timeout
Hey ADF fans! Here is a quick note on an important update that we will be making to ADF ... In Azure Data Factory and Azure Synapse Analytics, the default timeout for new pipeline activities is 7 days for most activities: In a few weeks, we are...
Released: Microsoft.Data.SqlClient 3.1.1
We have released an update to Microsoft.Data.SqlClient 3.1, version 3.1.1. The update addresses several issues that are important to our customers. Updates in Microsoft.Data.SqlClient 3.1.1 include: Fixed Fixed null SqlBinary as rowversion. #1700...
5G powered modern connected apps bring solutions to industry problems
Nicke McQuire, Director, Growth Innovation and Strategy at Microsoft recently published an article over on the Cloud Blogs site discussing how the future cloud will increasingly involve the intersection of 5G and AI to create a new application paradigm. He...
Most used SharePoint Framework solutions from the Store – July 2022
We are excited to see the continuous growth on the submissions of the SharePoint Framework solutions to the app source and on the usage of the SharePoint store. Given the significant number of new solutions, we want to acknowledge the top 10 most widely used...
Exchange Online Basic authentication is going away: What you need to know
Effective October 1, 2022, you will no longer be able to use Basic authentication to connect to Microsoft Exchange Online. If your organization uses server-side synchronization or the deprecated Dynamics 365 Email Router, you should find out now whether you need to...
CISA Adds Two Known Exploited Vulnerabilities to Catalog
CISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are a frequent attack vector for malicious cyber actors and pose significant risk to the federal enterprise....
Cisco Releases Security Update for Multiple Products
Cisco has released a security update to address a vulnerability affecting Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software. This vulnerability could allow a remote attacker to obtain sensitive information. For updates addressing lower...
#StopRansomware: Zeppelin Ransomware
5841ef35aaff08bb03d25e5afe3856a2 ffd228b0d7afe7cab4e9734f7093e7ba01c5a06e 1e3c5a0aa079f8dfcc49cdca82891ab78d016a919d9810120b79c5deb332f388 d6c4b253ab1d169cf312fec12cc9a28f 0f47c279fea1423c7a0e7bc967d9ff3fae7a0de8...
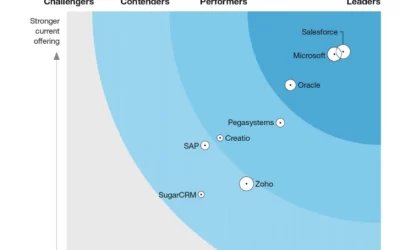
Microsoft is a Leader in The Forrester Wave: CRM Suites, Q3 2022
We are honored to announce that Microsoft Dynamics 365 was identified as a Leader in The Forrester WaveTM: CRM Suites, Q3 2022.A few weeks ago, during his Microsoft Inspire keynote, Satya Nadella reminded us of the distinct value that Microsoft provides to...
#StopRansomware: Zeppelin Ransomware
CISA and the Federal Bureau of Investigation (FBI) have released a joint Cybersecurity Advisory (CSA), #StopRansomware: Zeppelin Ransomware, to provide information on Zeppelin Ransomware. Actors use Zeppelin Ransomware, a ransomware-as-a-service (RaaS), against a wide...


Recent Comments