This article is contributed. See the original author and article here.
Learn all about how to get started in Cloud Discovery from Microsoft Cloud App Security in this deep dive article by guest author and Microsoft partner Sami Lamppu.
An Introduction to Cloud Discovery in Microsoft Cloud App Discovery (MCAS)
Cloud Discovery, which is one of the Microsoft Cloud App Security (MCAS) features, helps organizations to identity applications and user activities, traffic volume, and typical usage hours for each cloud application. In a nutshell, it can help to detect “Shadow IT” applications and possible risky applications.
This blog concentrates on the Microsoft Cloud App Security – ‘Cloud Discovery’ feature and its integration with Microsoft Defender for Endpoint (MDE) service. If you want to learn more about Microsoft Cloud App Security I encourage you to start from here: Cloud App Security Overview document.
Cloud Discovery Description:
The Cloud Discovery identifies cloud applications that the organization might not have visibility to, provides risk assessments and ongoing analytics and lifecycle management capabilities to control use. Cloud Discovery analyses the traffic logs and runs them against the cloud app catalog; to provide information on the discovered applications and the users accessing them.
Picture and description from Cloud App Security playbook.
Options for Ingesting Data
Cloud Discovery analyzes traffic logs against Microsoft Cloud App Security’s cloud app catalog of over 16,000 cloud apps. The apps are ranked and scored based on more than 80 risk factors to provide insights and visibility into applications used in the cloud, and the risk Shadow IT poses to the organization. At the time of writing the following options are available to ingest network traffic data to MCAS:
Snapshot reports
The snapshot reports provides ad-hoc visibility on traffic logs manually upload from firewalls and proxies.
Continuous reports
The following options are available for the continuous reports:
- Microsoft Defender for Endpoint integration (MDE)
- Log collector
- Secure Web Gateway (SWG) – such as ZScaler, iboss, Corrata and Menlo Security integration
Based on my personal experience, the Microsoft Defender for Endpoint (MDE) has been the selected solution in most cases I have worked. The main reason has been easy and smooth integration with the Microsoft Cloud App Security.
Cloud Discovery API
The Cloud Discovery API offers an option to automate traffic log upload and get automated Cloud Discovery report and risk assessment. You can also use the API to generate block scripts and streamline app controls directly to your network appliance.
Cloud App Security and Defender for Endpoint Integration – How It Works? (docs.microsoft.com)
The following chapters concentrate on MCAS & MDE integration benefits. The policy examples are based on the traffic information collected by the MDE service.
Cloud App Security uses the traffic information collected by Microsoft Defender for Endpoint (MDE) about the cloud apps and services being accessed from IT-managed Windows 10 machines. The native integration enables you to run Cloud Discovery on any machine in the corporate network, using public Wi-Fi, while roaming, and over remote access. It also enables machine-based investigation.
How Cloud Discovery Identifies the Apps?
Traffic data is analyzed against the Cloud App Catalog to identify more than 16,000 cloud apps and to assess their risk score. Active users and IP addresses are also identified as part of the analysis.
The current traffic detection model:
- The discovery of apps is achieved by comparing the destination URL/IP to a set of apps’ signatures, link.
Scenarios – Policy Examples
Here, I will go through some of the typical Cloud Discovery scenarios requested by customers I have worked with. Selected scenarios to identify apps from the cloud discovery data are:
- New cloud storage App
- New risky webmail application based on the risk score
In both scenarios, the App Discovery policies are used. The detection mechanism is based on the collected data, where MCAS creates alerts if a match is found based on the App Discovery policies.
Cloud Discovery Dashboard
The Cloud Discovery dashboard gives a nice overview of the collected data, possible alerts, and apps discovered in the network. Inside the marked area, you can find the apps and alerts created.
Application Details
When you select the application, you can see the detailed usage of the app. The App page includes overall information (+ alerts tab) of the application usage including the list of top rankings at the bottom of the page.
Cloud Discovery Policies
There are two kind of Cloud Discovery policies in MCAS:
- App Discovery policies
- App Discovery policy basically creates an alert when a new application is detected in the network.
- Additional parameters can be used to create the alert such as traffic in MB’s, the number of users, the application risk score among others.
- Discovery Anomaly detection policies
- Anomaly detection is enabled in out of the box rules.
- If fine-tuning is needed it can be done by customizing the built-in policy or creating a new custom policy.
In the policy configuration, you have a variety of options to configure your Cloud Discovery policy. In my example, I’m using the app “category” and “risk score”.
Example 1 – New App in Cloud Storage
Detect potential data exfiltration by a user to a cloud storage app and mark the app as unsanctioned.
Policy Configuration
In this example Cloud Discovery policy is configured with the following settings:
- Category: Cloud Storage
- Risk score: 0-5, means that the App risk score needs to be between 0-5. 10 means lower risk in the app, 0 means higher risk app based on the MCAS App catalog.
- Daily traffic: Greater than 50MB
- Number of users: Greater than 1
- Governance: Tag app as unsanctioned immediately if seen in the network
Alert
During the tests, I used different apps from the cloud storage category. The apps were StoreBigFile, Lucky Cloud, and FileDropper. All of the apps are found with a risk score of 2 from the Cloud App Security cloud app catalog.
When the traffic is received by MCAS, the data will be analyzed. If the traffic matches the Cloud Discovery policies alert is created in the MCAS instance.
As you can see from the below, the dashboard contains information about the traffic to the ‘FileDropper’ application. To perform a deeper analysis of the app usage, users, and devices, select the app for details. The best part is the integration between MCAS and MDE which allows you to see device information on the dashboards. This integration offers a smooth transition to the MDE portal when deep-dive investigation of network traffic is needed.
As configured, when the App is found (FileDropper) it’s marked as “unsanctioned” (red tag) by the governance actions in the example policy.
Example 2 – New Risky Webmail App Based on Risk Score – With Governance
With this policy, you can detect potential exposure of your organization to cloud apps that do not meet your security standards. The idea of this policy is to detect any App that risk score by App Catalog is below 3 and mark such App immediately as “unsanctioned”.
Policy Configuration
The policy is configured with the following settings:
- Risk score: 3 or below
- Apply to: All continuous reports (proxy + MDE endpoints)
- Number of users: Greater than 1 (for testing purposes, in the real environment this would be higher)
- Governance: Mark app as unsanctioned immediately when detected
Alert
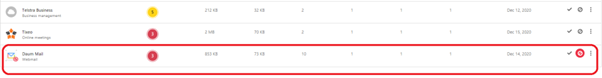
I tested a number of Webmail & also Online meeting applications with similar detection policies but in example pictures, there is “Daum” webmail used. When the data is received from the MDE service, the MCAS makes parsing to the data and creates an alert.
In the example case, “High” category alert received from the suspicious application used in my organization.
In the policy, governance action is configured. This means, that when the policy detects the app, the app is immediately tagged with the “Unsanctioned” tag.
Because of MCAS and MDE integration and, governance action to the application, the next time user browses to the ‘Daum’ webmail app it will be blocked by MDE from W10 devices. How cool is that? :)
This integration has some pre-requisites that I’m not covering here. If you need more information and want to establish it in your environment read more from here and here.
Blocking the Apps
Worth mentioning is, in general, Unsanctioning an app doesn’t block use of the app but enables to monitor its use more easily with the Cloud Discovery filters. Blocking the apps only works when accessing the app using a Windows 10 device with MDE configured, and MCAS & MDE integration has been configured.
The app marked as unsanctioned in MCAS should be found from MDE in a two (2) hours timeframe.
Block Script for On-Prem Appliances
Cloud App Security (MCAS) can help to block access to unsanctioned apps by using existing on-prem security appliances. Basically, you manage the apps in the MCAS end by tagging them as sanctioned/unsanctioned and create a dedicated block script and import it to the appliance. This solution doesn’t require redirection of all of the organization’s web traffic to a proxy. More information and how to establish the solution is found from the Microsoft docs article: “Export a block script to govern discovered apps”.
Considerations
There are a lot of development activities on-going in the MCAS and MDE services to deeper the integration and strengthen the security posture of the environment. I recommend following the MCAS updates from both, M365 Roadmap and What’s new in Cloud App Security pages for future updates.
Microsoft Zero Trust deployment guide for apps contains also a hint of what’s coming next in terms of app management (more granular controls).
MDE Integration
- If the endpoint device is behind a forward proxy, traffic data will not be visible to Microsoft Defender for Endpoint service (by default) and hence will not be included in Cloud Discovery reports.
- For more information, see Monitoring network connection behind a forward proxy.
- Cloud Discovery with MDE only works with the W10 devices that have pre-requisites filled.
- MDE allows 15.000 indicators per tenant
- Cloud discovery enables dive deep into the organization’s cloud usage, to identify specific instances that are in use by investigating the discovered subdomains.
- It takes up to two hours after you tag an app as Unsanctioned for app domains to propagate to endpoint devices
- By default, apps and domains marked as Unsanctioned in Cloud App Security will be blocked for all Windows 10 endpoint devices in the organization
- Currently, full URLs are not supported for unsanctioned apps. Therefore, when “unsanctioned” apps configured with full URLs, they are not propagated to Defender for Endpoint and will not be blocked. For example, google.com/drive is not supported, while drive.google.com is supported
- In-browser notifications may vary between different browsers
References
MCAS Deep dive into discovered apps
Integrate Microsoft Defender for Endpoint with Cloud App Security | Microsoft Docs
Sami Lamppu works for Nixu Corporation in Finland. He wrote the contents of this blog, edited by the MCAS team. Nixu is a cybersecurity services company that helps organizations embrace digitalization securely. https://www.nixu.com
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments