This article is contributed. See the original author and article here.
This blog is part three of a three-part series focused on business email compromise.
In the previous two blogs in this series, we detailed the evolution of business email compromise attacks and how Microsoft Defender for Office 365 employs multiple native capabilities to help customers prevent these attacks. In Part One, we covered some of the most common tactics used in business email compromise attacks, and in Part Two, we dove a little deeper into the more advanced attacks. The BEC protections offered by Microsoft Defender for Office 365, as referenced in the previous two blogs have been helping keep Defender for Office 365 customers secure across a number of different dimensions. However, to fully appreciate and understand the unique capabilities Microsoft offers, we need to take a step back.
Unparalleled scale
When we talk to customers about Microsoft Defender for Office 365, we always mention not only the size of our service, but the volume of data points we generate and collect throughout Microsoft. These things together help us responsibly build industry-leading AI and automation. Here are a few datapoints that can help put this into perspective:
- Every month, our detonation systems detect close to 2 million distinct URL-based payloads that attackers create to orchestrate credential phishing campaigns. Each month, our systems block over 100 million phishing emails that contain these malicious URLs.
- Every month, we detect and block close to 40 million emails that attempt to leverage domain spoofing, user impersonation, or domain impersonation – techniques that are widely utilized in business email compromise attacks.
- Clicking further into domain spoofing data, we observe that the majority of domains that send mail into Office 365 do not have a valid DMARC enforcement. That leaves them open to spoofing and that is why the Spoof Intelligence capability (as discussed in Part One) adds such a strong defense layer.
- In the last quarter, we rolled out new options in the outbound spam policy that have helped customers disable automated forwarding rules across 90% of Office 365 email accounts to further disrupt BEC attack chains.
- Additionally, our compromise detection systems are now flagging thousands of potentially compromised accounts and suspicious forwarding events. As we covered in our second blog, account compromise is a tactic used frequently in multi-stage BEC attacks. Learn more about how Defender for Office 365 automatically investigates compromised user accounts.
- Just in the last quarter, we have seen many customers implement “first-contact safety tips”, which have generated over 100 million phishing awareness moments. Learn more about first-contact safety tips.
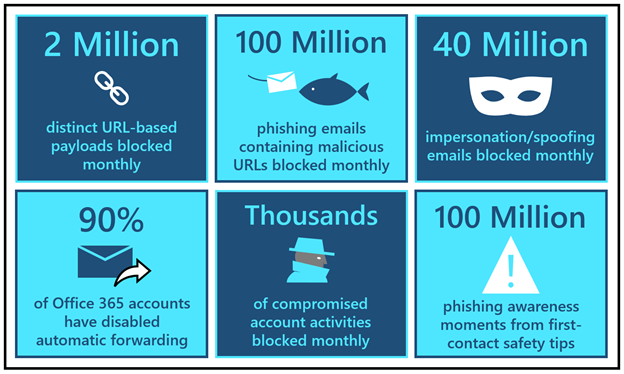 Figure 1: BEC by the numbers
Figure 1: BEC by the numbers
Artificial intelligence meets human intelligence
At Microsoft, we’re deeply focused on simplifying security for our customers, and we heed our own advice. We build security automation solutions that eliminate the noise and allow security teams to focus on the more important things. Our detection systems are being constantly updated through automated intelligence harnessed through trillions of signals, and this helps us focus our human intelligence on diving deep into the things that help improve customer protection. Our Microsoft 365 Defender Threat Research team leverages these signals to track actors, infrastructure, and techniques used in phishing and BEC attacks to ensure Defender for Office 365 stays ahead of current and future threats.
Leading the fight against cybercrime
Outside of the product, we also partner closely with the Digital Crimes Unit at Microsoft to take the fight to criminal networks. Microsoft’s Digital Crimes Unit (DCU) is recognized for its global leadership in using legal and technical measures to disrupt cybercrime, including attacks like BEC. By targeting the malicious technical infrastructure used to launch cyberattacks, DCU diminishes the capability of cybercriminals to engage in nefarious activity. In 2020, DCU directed the removal of 744,980 phishing URLs and recovered 6,633 phish kits which resulted in the closure of 3,546 malicious email accounts used to collect stolen customer credentials obtained through successful phishing attacks.
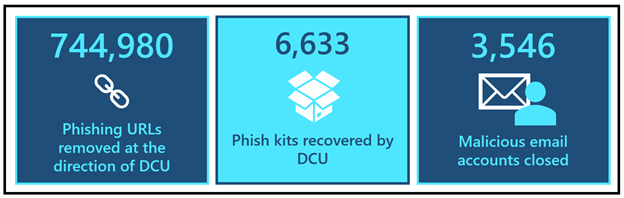 Figure 2: DCU by the numbers
Figure 2: DCU by the numbers
To disrupt cybercriminals taking advantage of the COVID-19 pandemic to deceive victims, in mid-2020, the Digital Crimes Unit took legal action in partnership with law enforcement to help stop phishing campaigns using COVID-19 lures. Additionally, with the help of our unique civil case against COVID-19-themed attacks, DCU obtained a court order that proactively disabled malicious domains owned by criminals. Read more about this here.
The DCU continues to leverage its expertise and unique view into online criminal networks to uncover evidence that informs criminal referrals to appropriate law enforcement agencies around the world who are prioritizing BEC because it is one of the costliest cybercrime attacks in the world today. In fact, since launching this blog series, the FBI released their 2020 Internet Crimes Report, which contains updated statistics on BEC related losses.
To learn more about DCU, take a look at a collection of articles here. You can also check out a recent episode of our Security Unlocked podcast where Peter Anaman, a Director and Principal Investigator for DCU, discusses what it’s like to investigate these BEC attacks.
Reducing the threat of business email compromise
We’ve covered quite a bit of content in this series and it feels only appropriate that we summarize the most important things that you can do to prevent BEC attacks in your environment. We’ve compiled these recommendations from a variety of sources, including industry analysts. The good news is that with Microsoft Defender for Office 365, you can now have one integrated solution that helps you easily adopt these recommendations.
Upgrade to an email security solution that provides advanced phishing protection, business email compromise detection, internal email protection, and account compromise detection
In the second blog in this series we covered the new ways in which attackers are orchestrating these dangerous attacks that are becoming increasingly difficult to detect with legacy email gateways or point solutions. Defender for Office 365 provides a modern, end to end, compliant protection stack that protects against advanced credential phishing, business email compromise detection, internal email filtering, suspicious forwarding detection, and account compromise detection. With Microsoft Defender for Office 365, you can detect these threats in your Office 365 environment without sending data out of your tenant, making it one of the simplest and most compliant ways to protect Office 365.
Complement email security with user awareness & training
With attacks evolving every day, it’s critical that we not only build tools to prevent attacks, but also that we train users to spot suspicious messages or indicators of malicious intent. The most effective way to train your users is to emulate real threats with intelligent simulations and engage employees in defending the organization through targeted training. With Defender for Office 365 we now provide rich, native, user awareness and training tools for your entire organization. Learn more about Attack simulation training in Defender for Office 365.
Implement MFA to prevent account takeover and disable legacy authentication
Multi-factor authentication (MFA) is one of the most effective steps you can take towards preventing account compromise. As we discussed previously, new BEC attacks often rely on compromising email accounts to propagate the attack. By Setting up multi-factor authentication in Microsoft 365 and implementing security defaults you can eliminate 99.9% of account compromise attempts.
Review your protections against domain spoofing
As we shared earlier, the majority of domains that send email to Office 365 have not properly configured DMARC. Leverage Spoof Intelligence in Defender for Office 365 to protect your users from threats that spoof domains that haven’t configured DMARC. Additionally, take the necessary steps to make sure your own domains are properly configured so that they aren’t spoofed. You can implement DMARC gradually without impacting the rest of your mail flow. Configure DMARC in Microsoft 365.
Implement procedures to authenticate requests for financial or data transactions and move high-risk transactions to more authenticated systems
We use email and collaboration tools to perform a wide variety of tasks, and sharing financial data doesn’t need to be one of them. To minimize the risk of accidental sharing of sensitive information like routing numbers or credit card information, consider using Data Loss Prevention policies in Office 365. Additionally, consider, establishing a process that moves these transactions to a different system – one designed specifically for this purpose.
Closing thoughts
At Microsoft, we embrace our responsibility to create a safer world that enables organizations to digitally transform. We’ve put this blog series together with the goal of reminding customers not only of the significance of BEC, but the wide variety of prevention mechanisms available to them. If you’re looking for a comprehensive solution to protect your organization against costly BEC attacks, look no further than Microsoft Defender for Office 365.
Day in and day out, we relentlessly strive to enhance our security protections to stop evolving threats. We are committed to getting our customers secure – and helping them stay secure.
Do you have questions or feedback about Microsoft Defender for Office 365? Engage with the community and Microsoft experts in the Defender for Office 365 forum.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments