This article is contributed. See the original author and article here.
Having a background in education, I do a lot of work with education customers who are looking to improve on their information protection capabilities. Building a business case for sensitivity labelling and related features can be difficult without first understanding the existing information protection issues and the risks that labelling can help to address. Towards this, I’ve put together a series of points backed up with education-specific examples to demonstrate why information protection should be high on our list of priorities. I hope this might be useful in helping organisations understand the need for these capabilities and allow them to better articulate this back to business stakeholders.
If you haven’t come across Sensitivity Labelling before, it’s just what its name implies. Its most basic form allows us to apply a label to sensitive information to mark it as such (this is probably more traditionally referred to as classification, but we’ll avoid using this terminology). Once we have our sensitive information labelled, there are various things that we can do with it. Below, we’ll explore some of these possibilities and the risks that the configuration can help to mitigate.
Decisions, decisions…
There’s a lot to be said for the simple and utterly non-technical process of applying sensitivity labels to information. When we’re required to apply a label, there’s a mental process that we put ourselves through to determine which label might be appropriate. It’s easy to draw this process up into a decision tree with decreasing levels of sensitivity:
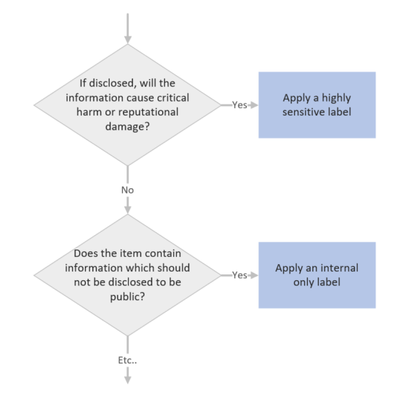
When we implement sensitivity labelling, we’re asking users to consider the risk of information. We’re educating them to consider which information may or may not be appropriate for certain audiences. This process, which over time becomes second nature, will do a lot to help organisations secure their data as it instils users with a practice of continual information risk assessment. This is useful, not only in a work context, but also in staff personal lives as people who often think about information security will be more likely to stop and think before falling for a phishing campaign or oversharing risky details on social media.
I find these differences in staff mentality evident as I move between customer environments delivering security workshops. Customers with staff who continually apply classifications to information, such as those in the government sector, will typically have a much higher awareness of information risk. Non-government customers may have similar privacy requirements documented in their policies which, if they’re lucky, staff might read during onboarding but are unlikely to think about during their day-to-day work activities. By implementing labelling we’re bringing these policies to the forefront and requiring staff to continually assess information risk which will help to build a more risk-aware organisational culture.
Business Case Point 1: Implementing sensitivity labelling will help to instil a culture of information protection.
Back it up with automation
So, when we implement labelling, we can expect that we may have some disruption on day 1 as we’re asking staff to stop and think before selecting a label. This will fairly quickly become second nature for most users, however, we’re all human and we have to expect that occasionally someone might select the wrong label. We also have to allow for unengaged users and new staff that haven’t been provided with training. To help ensure accurate labelling we have auto-labelling capabilities that can be enabled to assist with label selection. With auto-labelling policies, we can check for what are referred to as ‘Sensitive Information Types’, which are pieces of information that can help us to make a decision on the sensitivity of an item. If we see an item that contains student Personally Identifiable Information (PII), then we can either automatically set the item to ‘Confidential’ or help to educate the user by suggesting that they choose the ‘Confidential’ label. Sensitive information types are quite powerful and we can create some really granular rules checking, for example, the proximity between a code and a keyword that is required for an item to be considered a match. This can help us to weed out false positives and ensure label accuracy.
Within Education, we’d typically be configuring student numbers, staff employee ID’s, student email addresses, records numbers and anything that might relate to medical information as sensitive information types. In addition to this, a standard deployment would look for bank details, credit card numbers, medical details, tax file numbers, social security numbers, etc. If we detect any of these information types in a file or email, then we would either automatically set a label or recommend an appropriate label to the user.
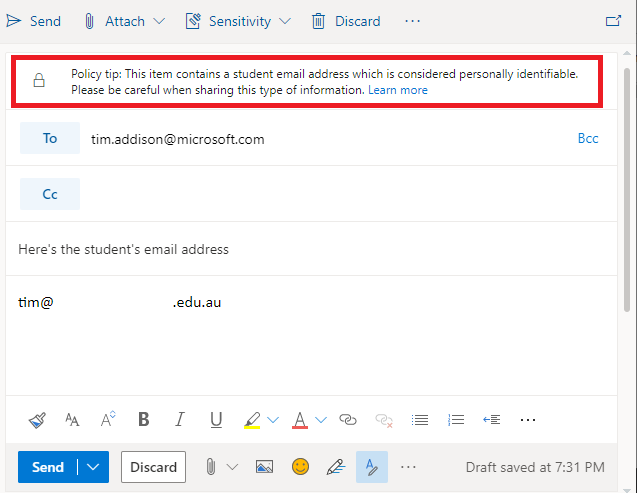
Auto-labelling is a great way of helping to educate staff on correct label usage, ensuring label accuracy and dealing with what I like to refer to as the ‘lazy staff factor’. The example that I typically give, bearing in mind that I have no data to back this up, is that via manual labelling we may achieve 70% label accuracy. When we supplement the approach up with targeted training and auto-labelling, we should be able to hit 90-100% label accuracy, which is great because we can then start capitalizing on this via the following features.
Where is your sensitive information?
Such a simple question that will, and should, terrify a lot of people. I think that this is also something that is commonly overlooked as an advantage to labelling implementation. I’m sure most of us have worked in environments with data sprawled across a range of mapped drives, network shares, portable USB drives, personal email accounts and various cloud services.
With data spread around like this, how can we be sure that we aren’t leaking information? Identifying the items that contain sensitive information across these locations is probably unrealistic due to the amount of effort required, is the best way to turn this around because once implemented we can ensure that all new information is labelled, we can monitor, warn or block the flow of sensitive information inside and outside of our organisation, helping to keep information in the intended location. We can even browse each of our services by a label to, for example, see where all ‘Restricted’ files are stored across SharePoint and Teams (Note also that there are ways to apply labels to legacy data locations, but we’ll save that one for another day).
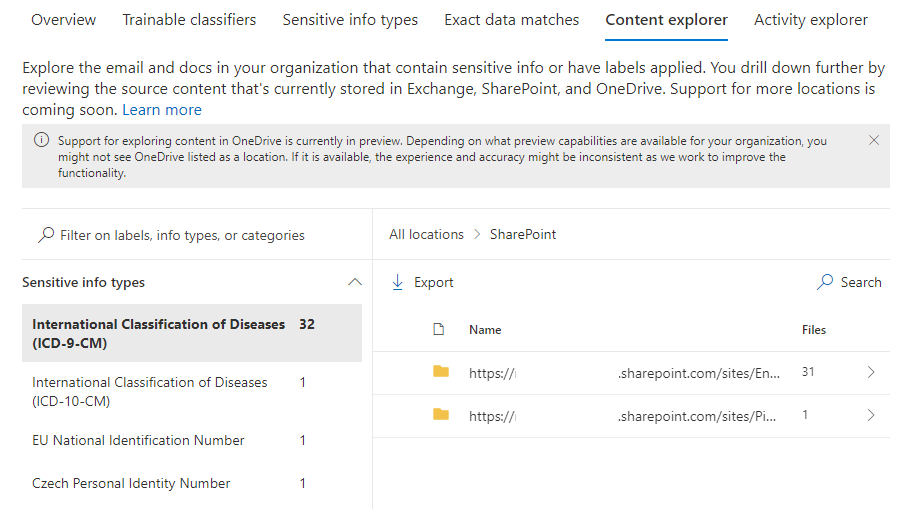
Business Case Point 2: Sensitivity Labelling will allow us to find all of our sensitive information.
Sensitivity Indicator
This is one of the most straightforward configurations available to labelling and yet so important. Once a label has been applied to an item, anyone viewing that item will instantly get a visual indication of its sensitivity. A watermark, header or footer can give readers a clear statement that an item is sensitive without them needing to read it in full. This could be as simple as a watermark or a big red ‘Confidential’ across the top of a page or email.
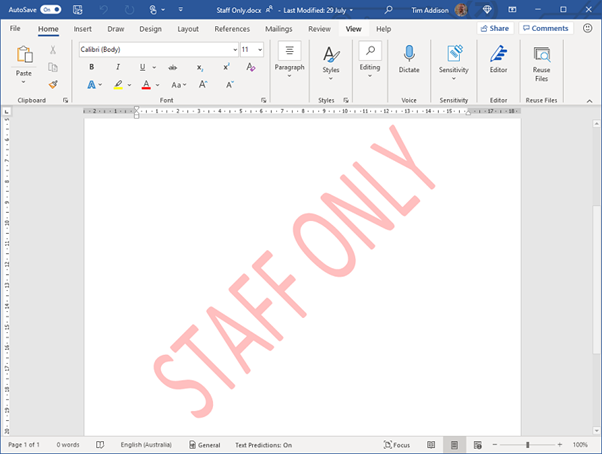
We need to be extremely careful when dealing with student information, but particularly with information of a personal nature such as student medical information. There may be situations where we need to pass these types of information on to a third party, for example, when we need to advise an external event organizer of a student’s medical condition. Marking these types of correspondence as ‘Confidential’ may remind the staff member to double-check the recipient’s address before sending the email and remind the recipient of their obligation to keep this information private.
Business Case Point 3: Sensitivity Labelling will provide information readers with a clear visual representation of the item’s sensitivity.
Monitor and Control the Flow of Sensitive Info
Let’s assume by this point that we’ve decided to implement labelling and are now applying a label to indicate the sensitivity of all new documents and emails. The next component that we might want to configure is Data Loss Prevention (DLP). With this tool, we’re able to implement policies to monitor the flow of sensitive information and apply rules to block or caution users when they try to send it to inappropriate audiences. Let’s think about the various situation where these capabilities might be useful:
- A staff account is compromised by an external attacker who then exfiltrates all student information from the student management system.
- An internal discussion regarding a student’s welfare and possible issues in their home environment is accidentally sent to the parent.
- An executive staff member’s account is compromised via target phishing and used to ask administrative staff for bank account login details. Funds are then transferred out of the bank account.
- An office staff member who is not aware of organisational policy saves parent credit card details to a file where they may be later accessed. The file is in a shared location and is accessed by other users.
Sadly, a lot of these situations are quite common in Education and organisations are unaware that they can be prevented with some very simple configuration. In each of the above situations, DLP policies could be put in place to:
- Warn users that the action may be against policy,
- Alert the user (which may be relevant for compromised accounts) and administrators that a policy violation has occurred, and
- Block the transmission, sharing or saving of sensitive information.
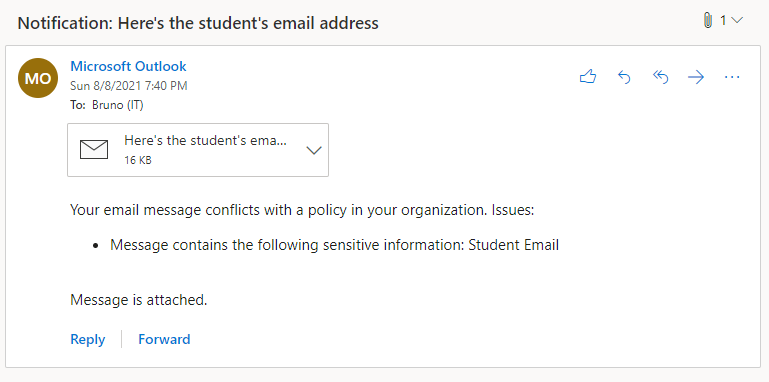
Business Case Point 4: Sensitivity Labelling will help to prevent sensitive information from being passed to unauthorized users.
The High Cost of Data Breach
Here in Australia, we have some fairly stringent laws which require us to advise a government body and those affected whenever we make a significant breach of privacy. These data breaches can come with fines, can be costly in terms of resources required to remediate them and can damage the reputation of our institutions. For private education organisations and universities, loss of reputation has the potential to impact enrollments. Universities are often in competition for research grants and a data breach may impact grant eligibility which could have a flow-on impact on the institution’s financial viability. Lastly, information breaches may come with a high legal cost as those that the information was about may choose to take legal action against the offending organisation. The data loss prevention methods that I mentioned in the previous section can do a lot to help protect organisations from significant data breaches.
Business Case Point 5: Sensitivity Labelling will help to protect reputation by reducing the likelihood of data breaches.
Containerisation
A relatively new capability that we can implement via labelling is the labelling of locations within our environment. The way this works is that we treat a Team or a SharePoint site as a ‘container’ and we assign a label to it which signifies the highest sensitivity of items that should exist within it. If an item with greater sensitivity than permitted for the container is moved there then we let the user know that the location is not safe and, if desired, kick off remediation activities.
The most obvious example of how this can be useful in education is to help prevent sensitive ‘Staff Only’ data from being saved to student accessible locations. This could be academic information, student medical info, quiz answers, etc. It doesn’t really matter what it is, if it’s considered sensitive then students probably shouldn’t be accessing it. Containerisation is one of the best ways that we can keep these types of information out of student reach (Note, however, that at the time of writing, there is still some lack of support for this within class
templated teams).
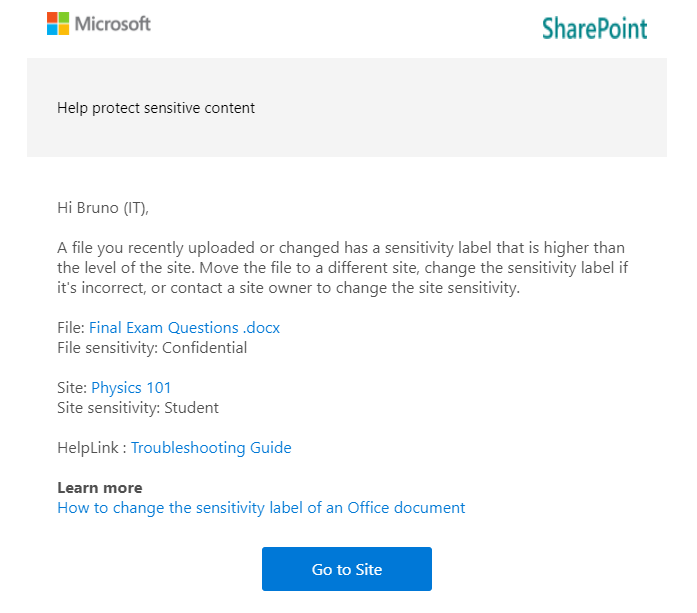
Business Case Point 6: Sensitivity Labelling will help to keep sensitive information out of student reach.
Safe External Collaboration
There’s one more important use for containerisation which relates to guest access. Guest access is a way that we can allow external users, such as those from other organisations (or just anyone with an email address depending on the configuration), into our environment so that we can collaborate with them. We might, for example, have volunteers, parents, school committee members or other members of the public, that we want to give access to an internal service (e.g., a web portal), involve in school-based discussion, or work on files with. Via the more traditional approaches to collaboration, we might create full accounts for them, which will have a licensing cost and will probably result in them gaining more access than they really require (to internal directories for example). Alternatively, we may email them copies of documents which still slow down our collaboration, not to mention result in us potentially sending sensitive information outside of our environment rather than keeping it inside where access can be controlled.
For universities or customers that have a separate Office 365 tenant per organisation, a common use of guest access is to enable project collaboration with another educational institution. When used in this way, users from both organisations can discuss and work on a single set of documents within a Team.
Guest access is a great way to make all of the collaboration capabilities that Microsoft 365 offers to internal users also available in interactions with external users, but if the correct governance practices are not applied then it can introduce some risks. For example, a guest could be accidentally added to a Team that includes students, enabling guest to student interaction. It may be hard for us to maintain the duty of care in such a situation as a staff member may not always be available to screen channel discussion, so we probably need to look at locking guests out of student accessible Teams. This is another capability that labelling enables as we can apply policies to restrict guests from accessing Teams with certain labels (No support for class templated teams with this yet but it’s possible to work around via ‘AllowToAddGuests’ in PowerShell. Additional blog post on the way.).
Business Case Point 7: Sensitivity Labelling will allow for guest collaboration to be enabled without compromising student safety.
Lock up the Guests
Regarding guest access to information stored in sensitive locations, there are two additional risks that we need to consider:
- A case of mistaken identity might mean that a guest is added to a team that contains sensitive information.
- Sensitive files could accidentally be saved to a location where guests have been given access.
As covered under the previous point, with sensitivity labelling we are able to lock guests out of certain teams which will also help to protect our sensitive information from cases of mistaken identity. Additionally though, because we’re likely to restrict guest access to our most sensitive labels and labelled locations, when a high sensitivity file is saved to a low sensitivity, guest accessible location, we’ll warn users and potentially kicking off remediation activities. So, we’re helping to keep guest users out of sensitive files and locations.
Business Case Point 8: Sensitivity Labelling will allow us to keep guest users out of sensitive files and locations.
Restrict Access to Files
The last category of capabilities that I want to mention is around access restriction. Most of the benefits and controls that I’ve mentioned to this point assume that your sensitive information is stored within your Office 365 environment. It’s much easier to have control of your information when it’s housed in a well-governed platform. But what about situations where:
- We have very sensitive information that we need to ensure won’t be accessed by unauthorized users, regardless of their location.
- We need to make sure that only the intended recipient of an email can access it.
- We need to set up highly secure communication with a partner organisation that we need to share sensitive information with.
This is where encryption comes into play. The most straightforward use of encryption in sensitivity labelling is to apply it to all items that have a particular label. When we do this, only users which we’ve specified in our label configuration are able to access it. The perfect example of this would be a ‘Staff-only’ label which is only accessible to the staff group.
If a document with this label applied was copied elsewhere or misplaced via a lost USB drive, then it wouldn’t matter as anyone attempting to open the file that isn’t on the list of approved users will not be given access. Encryption has typically come with some downsides, particularly with regard to collaboration as encrypting a file would prevent document co-editing, but there are some amazing new preview capabilities now available which eliminate these disadvantages and which will lead to this configuration being much more commonplace.
Within education, label-based encryption might be useful for blocking access to the most sensitive of information. Data relating to child protection matters, HR or ongoing police investigation may be good candidates for this. Universities may want to consider applying encryption to highly confidential research data, intellectual property or other information assets that, if breached could result in financial loss.
Business Case Point 9: Sensitivity Labelling will allow us to lock unauthorized users out of highly sensitive information regardless of their location.
Secure Correspondence with Partner Organisations
We may have a need to send sensitive information to an external recipient. Email is generally considered a fairly unsafe platform. There’s the risk that mail may be intercepted along the way or forwarded to an unintended recipient. Mail encryption protocols are also opportunistic and if you’re sending to an organisation that doesn’t have a handle on their mail security then there’s risk that your sensitive email may be transmitted in plain text making it a lot easier to intercept.
Via labelling, there are a few things that we can do to ensure that our sensitive correspondence can’t be intercepted or passed on to an undesired recipient. Via a service called Office Message Encryption (OME) we can implement a rule which would encrypt all emails with a particular label applied. If the email is destined for an organisation that is also running Office 365, then the encryption is seamless and the recipient will see the fully encrypted email as they would any other, with the addition of your sensitivity markings and other warning tooltips.
For universities and larger education providers, we can use this to enable the secure transfer of sensitive information with our partners, which could be other school districts, universities or government authorities.
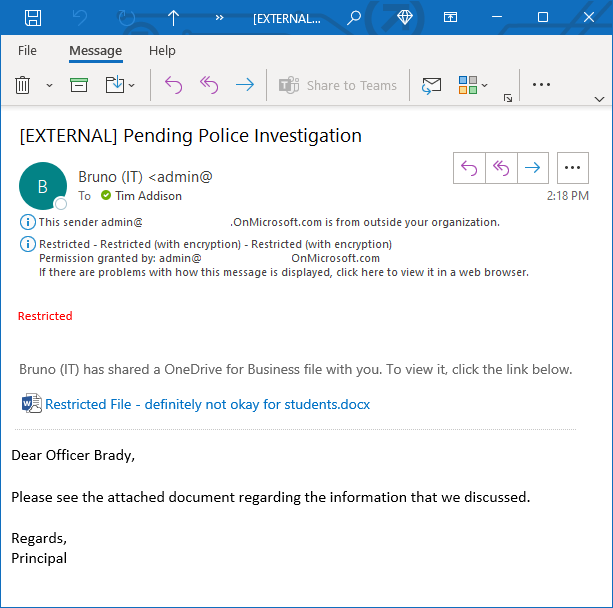
Business Case Point 10: Sensitivity Labelling will enable the secure transfer of sensitive information with partner organisations.
Secure Messaging to Parents and Students
Building on the previous topic, what if the recipient is using another mail platform or an anonymous email account, then the experience isn’t quite as seamless. How OME works in these situations is that Exchange Online will send the recipient a message with a link to a portal. When the recipient accesses the portal, it will require them to either verify their identity or, if it’s their first visit, set up Multi-Factor Authentication so that their identity can be better verified next time around. The recipient can then read and interact with the message from within the web portal.
There are many uses for this style of secure communication within education. A ‘Recipient Only’ label which applies message encryption could be added to all sensitive school to parent correspondence. This would keep the correspondence secure regardless of the security of the parent’s email account or home computer. For universities, this can be a great way to enable secure communication with new or potential students who might not yet have access to a university email account.
Business Case Point 11: Sensitivity Labelling will provide a method for the sending of secure correspondence to parents or students.
Summary
There are a lot of benefits and a lot of different ways that sensitivity labelling can help secure the sensitive information of educational institutions. In this article, I’ve covered what I see as the key points and items that should be the focus of a business case. However, there are many other capabilities that will also be applicable; trainable classifiers, exact data match, purview, conditional access and endpoint DLP to name a few but we’ll need to save those for another time.
In conclusion, implementing sensitivity labelling will:
- Help to instil a culture of information protection.
- Allow us to find all of our sensitive information.
- Provide information readers with a clear visual representation of an item’s sensitivity.
- Help to prevent sensitive information from being passed to unauthorized users.
- Help to protect reputation by reducing the likelihood of data breaches.
- Help to keep sensitive information out of student reach.
- Allow for guest collaboration to be enabled without compromising student safety.
- Allow us to keep guest users out of sensitive files and data locations.
- Allow us to lock unauthorized users out of highly sensitive information regardless of its location.
- Enable the secure transfer of sensitive information with partner organisations.
- Provide a method for the sending of secure correspondence to parents or students.
If you’re interested in learning more about sensitivity labelling and other Microsoft Information Protection features, I recommend the following links:
- Learn about sensitivity labels – Microsoft 365 Compliance | Microsoft Docs
- Learn about data loss prevention – Microsoft 365 Compliance | Microsoft Docs
- Sensitivity labels for Microsoft Teams – Microsoft Teams | Microsoft Docs
- Sensitivity labeling and protection in Outlook for iOS and Android | Microsoft Docs
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments