This article is contributed. See the original author and article here.
This blog post contains important information about TLS certificate changes for Azure IoT Hub and DPS endpoints that will impact IoT device connectivity.
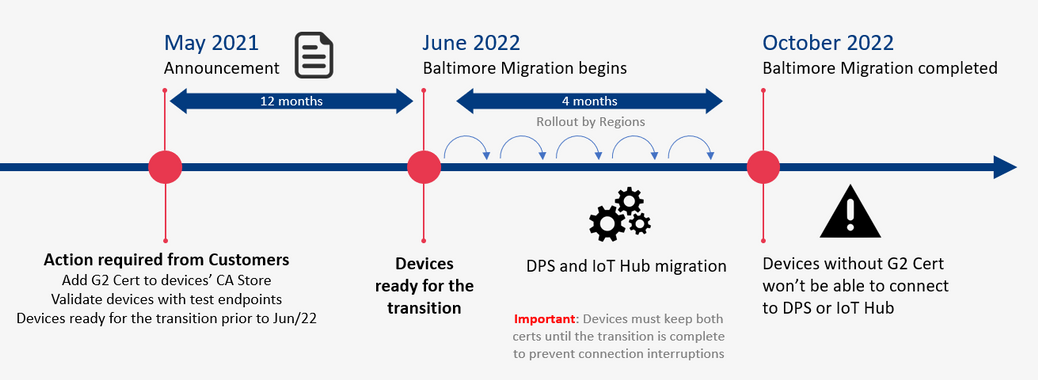
In 2020 most Azure services were updated to use TLS certificates from Certificate Authorities (CAs) that chain up to the DigiCert Global G2 root. However, Azure IoT Hub and Device Provisioning Service (DPS), remained on TLS certificates issued by the Baltimore CyberTrust Root. The time has come now to switch from the Baltimore CyberTrust CA Root for Azure IoT Hub and DPS, which will migrate to the DigiCert Global G2 CA root starting in June 2022, and finish by or before October 2022. This change is for these services in public Azure cloud and does not impact sovereign clouds.
Why is this important? After the migration is complete, devices that don’t have DigiCert Global G2 won’t be able to connect to Azure IoT anymore. You must make certain your IoT devices include the DigiCert Global G2 root cert by June 30, 2021 to ensure your devices can connect after this change.
We expect that many Azure IoT customers have devices which will be impacted by this IoT service root CA update; specifically, smaller, constrained devices that specify a list of acceptable CAs.
The following services used by Azure IoT devices will migrate from the Baltimore CyberTrust Root to the DigiCert Global G2 Root starting June 1, 2022 completing on or before Oct 2022.
- Azure IoT Hub
- Azure IoT Hub Device Provisioning Service (DPS)
If any client application or device does not have the DigiCert Global G2 Root in their Certificate Stores, action is required to prevent disruption of IoT device connectivity to Azure.
Action Required
- Keep using Baltimore in your device until the transition period is completed (necessary to prevent connection interruption).
- In addition to Baltimore, add the DigiCert Global root G2 to your trusted root store.
- Make sure SHA384 for Server certificate processing is enabled on the device.
How to check
- If your devices use a connection stack other than the ones provided in an Azure IoT SDK, then action is required:
- To continue without disruption due to this change, Microsoft recommends that client applications or devices trust the DigiCert Global G2 root:
- To prevent future disruption, client applications or devices should also add the following root to the trusted store:
Microsoft RSA Root Certificate Authority 2017
(Thumbprint: 73a5e64a3bff8316ff0edccc618a906e4eae4d74)
- If your client applications, devices, or networking infrastructure (e.g. firewalls) perform any sub root validation in code, immediate action is required:
- If you have hard coded properties like Issuer, Subject Name, Alternative DNS, or Thumbprint, then you will need to modify this to reflect the properties of the new certificates.
- This extra validation, if done, should cover all the certificates to prevent future disruptions in connectivity.
- If your devices (a) trust the DigiCert Global G2 root CA among others, (b) depend on the operating system certificate store that has OS updates enabled for getting these roots or (c) use the device/gateway SDKs as provided, then no action is required, but validation of compatibility would be prudent:
- Please verify that your respective store contains both the Baltimore and the Global G2 roots for a seamless transition:
- Ensure that the device SDKs in use, if relying on hard coded certificates or on language runtimes have the DigiCert Global G2 root as appropriate.
- Please verify that your respective store contains both the Baltimore and the Global G2 roots for a seamless transition:
Validation
We ask that you perform basic validation to mitigate any unforeseen impact to your IoT devices connecting to Azure IoT Hub and DPS. We are providing test environments for your convenience to verify that your devices can connect before we update these certificates in production environments.
This test can be performed using one of the endpoints provided (one for IoT Hub and one for DPS).
A successful TLS connection to the test environment indicates a positive result outcome – that your infrastructure and devices will work as-is and can connect with these changes. The credentials contain invalid data and are only good to establish a TLS connection, so once that happens any run time operations (e.g. sending telemetry) performed against these services will fail. This is by design since these test resources exist solely for customers to validate device TLS connectivity.
The credentials for the test environments are:
- IoT Hub endpoint: g2cert.azure-devices.net
- Connection String: HostName=g2cert.azure-devices.net;DeviceId=TestDevice1;SharedAccessKey=iNULmN6ja++HvY6wXvYW9RQyby0nQYZB+0IUiUPpfec=
- Device Provisioning Service (DPS):
- Global Service Endpoint: global-canary.azure-devices-provisioning.net
- ID SCOPE: 0ne002B1DF7c
- Registration ID: abc
If the test described above with the TLS connection is not sufficient to validate your scenarios, you can request the creation of devices or enrollments for tests in special canary regions by contacting the Azure support team (see Support below).
The test environments will be available until all public cloud regions have completed their update to the new root CA.
Support
If you have any technical questions on implementing these changes or to request the creation of your own device or enrollment for tests, please open a support request with the options below and a member from our engineering team will get back to you shortly.
- Issue Type: Technical
- Service: Internet of Things/IoT SDKs
- Problem type: Connectivity
- Problem subtype: Unable to connect.
Certificate Summary
The table below provides information about the certificates that are being updated. Depending on which certificate your device or gateway clients use for establishing TLS connections, action may be needed to prevent loss of connectivity.
Certificate | Current | Post Update (June 1, 2022 – October 1, 2022) | Action |
Root | Thumbprint: d4de20d05e66fc53fe1a50882c78db2852cae474 OU = CyberTrust | Thumbprint: df3c24f9bfd666761b268073fe06d1cc8d4f82a4 Expiration: Friday, January 15, 2038 5:00:00 AM Subject Name: CN = DigiCert Global Root G2 OU = www.digicert.com O = DigiCert Inc C = US | Required |
Intermediates | Thumbprints:
CN = Microsoft RSA TLS CA 01 Thumbprint: 417e225037fbfaa4f95761d5ae729e1aea7e3a42 ——————————————————————————— CN = Microsoft RSA TLS CA 02 Thumbprint: b0c2d2d13cdd56cdaa6ab6e2c04440be4a429c75 ———————————————————————————
Expiration: Tuesday, October 8, 2024 12:00:00 AM; O = Microsoft Corporation C = US | Thumbprints:
CN = Microsoft Azure TLS Issuing CA 01 Thumbprint: 2f2877c5d778c31e0f29c7e371df5471bd673173 ——————————————————————————– CN = Microsoft Azure TLS Issuing CA 02 Thumbprint: e7eea674ca718e3befd90858e09f8372ad0ae2aa ——————————————————————————– CN = Microsoft Azure TLS Issuing CA 03 Thumbprint: 6c3af02e7f269aa73afd0eff2a88a4a1f04ed1e5 ——————————————————————————– CN = Microsoft Azure TLS Issuing CA 04 Thumbprint: 30e01761ab97e59a06b41ef20af6f2de7ef4f7b0 ——————————————————————————–
Expiration: Friday, June 28, 2024 5:29:59 AM Subject Name: O = Microsoft Corporation C = US | Required |
Leaf (IoT Hub) | Subject Name: CN = *.azure-devices.net | Subject Name: | Required |
Leaf (DPS) | Subject Name: CN = *.azure-devices-provisioning.net | Subject Name: | Required |
Note: Both the intermediate and leaf certificates are expected to change frequently. We recommend not taking dependencies on them and instead trust the root certificate.
Brought to you by Dr. Ware, Microsoft Office 365 Silver Partner, Charleston SC.


Recent Comments